May 12, 2025
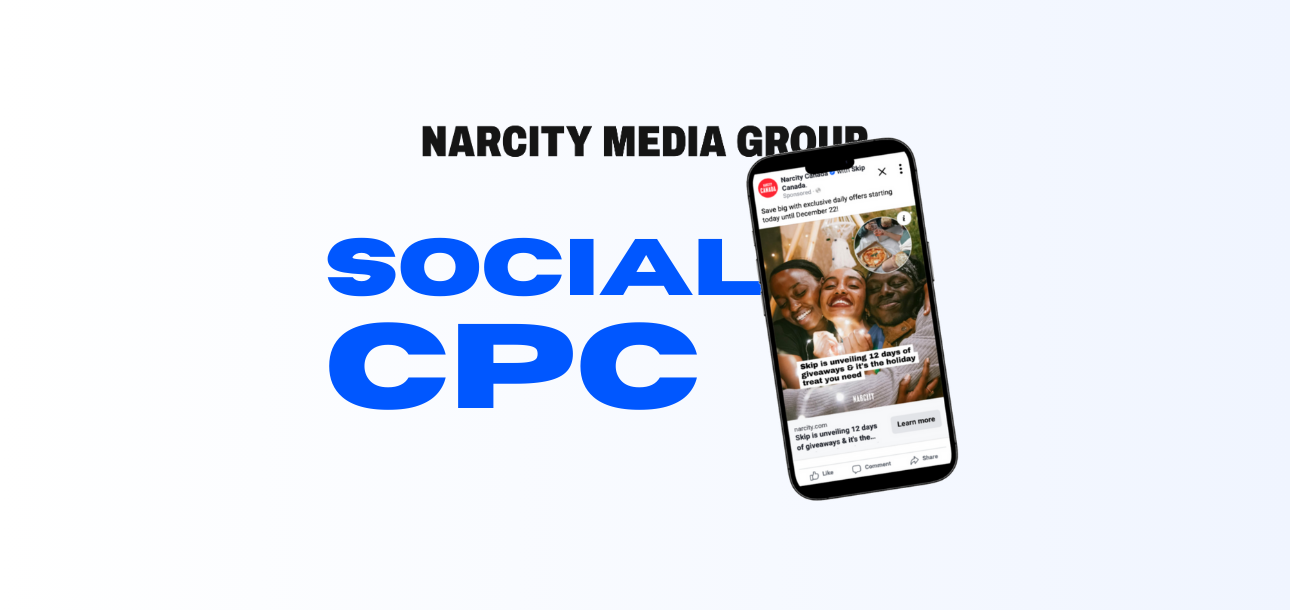
Introducing Social CPC: our new performance ad product
Drive tangible results with our new mid-funnel advertising product....keep reading

May 12, 2025
Drive tangible results with our new mid-funnel advertising product....keep reading